Bypassing Root Detection in Three Intouch
Three recently released “InTouch”, an application for Android and iOS that allows you to use a WiFi network to send/receive phone calls and text messages, meaning that you can continue to use your phone as a phone without having a cellular network connection.
Unfortunately for me, Three decided not to allow rooted devices to use the application – launching the app on a rooted device resulted in a “It seems that the device is rooted. This application can not run on rooted device” error.
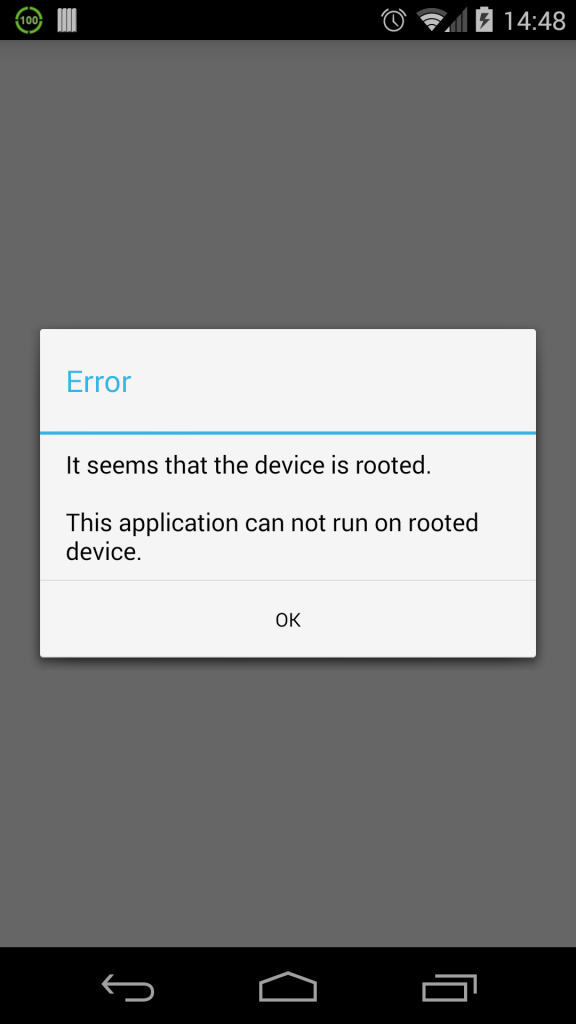
Not wanting to miss out on being able to use their application (my house is a signal deadzone), and being unwilling to un-root my phone, I decided to explore other avenues.
Firstly, I downloaded the APK file from my phone using adb:
adb pull /data/app/com.hutchison3g.threeintouch-1.apk
I then decompiled the application into Smali using apktool, by running the following command:
apktool d com.hutchison3g.threeintouch-1.apk
This created a new folder with the same name as the APK file. Inside that folder was another folder called smali, which contains the smali disassembly of the APK.
A simple grep for the string “root” was all that was needed to find the sections of the disassembly responsible for root detection:
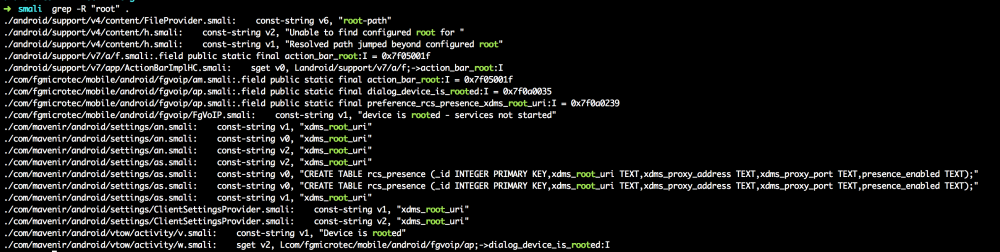
The relevant lines were those containing “device is rooted” – in this case, “v.smali” and “FgVoIP.smali”. Opening up FgVoIP.smali and searching for the line containing the word “root” gave me some context:
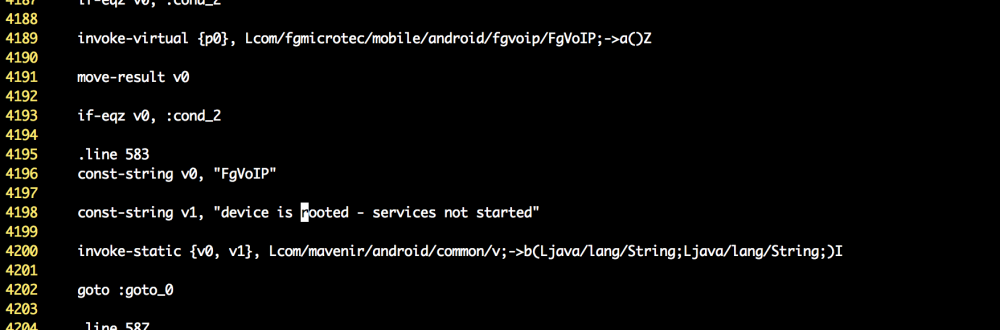
Line 4193 is an if statement, checking if the register v0 is equal to zero. The value of v0 is return value of the method invoked on line 4189. In the case that v0 is equal to zero, execution jumps to whatever is at the label :cond_2 – if v0 is anything other than 0, then a string mentioning “device is rooted” is defined, and passed to another method. With that in mind, it’s fair to say that a() in the FgVoIP class is probably their “root checking” method.
An easy way to patch this root detection out is to modify the if statement on 4193 to make it unconditional. I did this by replacing if-eqz v0, :cond_2 with goto :cond_2:
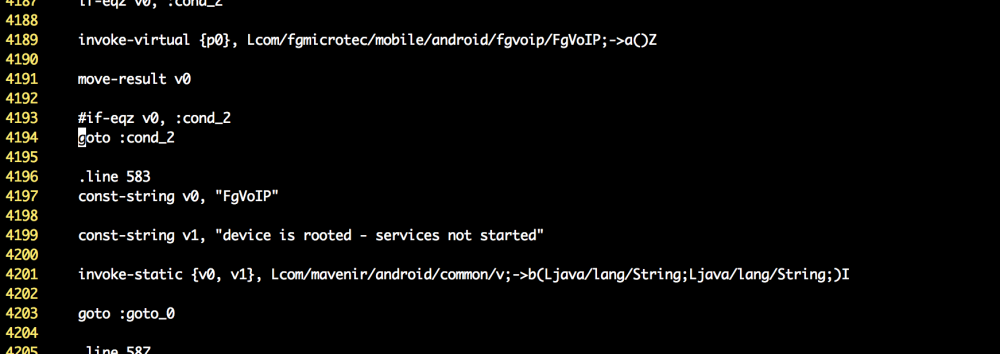
I then repeated a similar process on “v.smali”.
Once I had modified the two smali files to skip the root detection, I needed to re-compile the apk file so that I could install it on my device. I accomplished this by running:
apktool b com.hutchison3g.threeintouch-1 -o com.hutchison3g.threeintouch-1-patched.apk
However, the resultant APK was un-signed. In order to install the APK onto my device, I needed to generate a key and sign the APK. I did this by following the instructions for “Signing Your App Manually” on the Android SDK documentation.
Once I had signed my app, I was able to install it by running adb install com.hutchison3g.threeintouch-1-patched.apk. I was then able to launch and use the Three InTouch app without any problems.
It’s worth noting that I did this as a learning exercise, and don’t recommend that you necessarily go out there and do this yourself. Similar techniques can be used to bypass root detection in many Android Applications.