Ebay XSS
Earlier in the year, I discovered an XSS vulnerability in the Selling Manager section of the eBay.
The problem was caused by improper escaping of the URL’s GET parameters, which were reflected back on on the page. When choosing the “drafts” section of the session manager, I noticed that several parameters appeared in the URL:
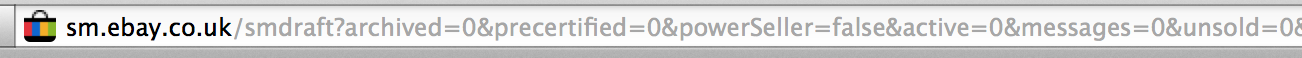
Naturally (after confirming that eBay allowed such testing), I tried modifying these parameters – to my surprise, the page happily showed my new, update values (although they weren’t saved server-wide). I could modify my feedback score, message count, inventory counts etc to contain invalid characters, such as letters. Unfortunately, eBay was escaping the strings to remove anything that would allow cross-site scripting – or so I thought.
After some more playing, I accidentally included a URL parameter twice. Again, to my surprise, the page showed both values, but separated by commas – however, this time the second value was not being escaped. By setting the duplicate parameters value to be a snippet of javascript, I could run malicious code in the context of sm.ebay.co.uk.
Combined with a phishing attack, an attacker could easily exploit this vulnerability to steal money from a user, gain access to their account and/or cause all kinds of trouble.
I reported this vulnerability to the “eBay inc Bug Bounty” on the 30th of May, and after some prodding, received an email back telling me that the eBay Inc bug bounty didn’t cover the eBay website. The problem then got forwarded on other eBay Bug Bounty. Fast forward to mid-July, I was asked for an example URL that would trigger the XSS (which I had included in my original report, but must have somehow got lost). I have not heard anything from eBay since, but the problem now seems to have been fixed.